This week, the tech world was rocked by several significant security revelations, including a major flaw in Apple’s hardware, warnings of cyberattacks on US water systems, the emergence of new Russian malware, and ongoing global hacking campaigns linked to China.
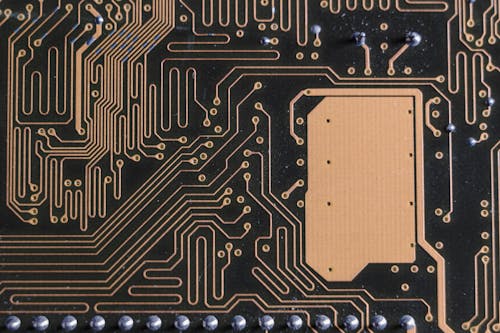
Firstly, researchers uncovered a critical flaw in Apple’s M-series chips, affecting Mac computers. Dubbed “GoFetch,” the exploit leverages a flaw in the chips’ data memory-dependent prefetcher (DMP), potentially allowing attackers to extract secret encryption keys. This flaw, present in M1, M2, and M3 chips, poses a significant challenge as it resides within the silicon itself, making it virtually unpatchable.
Meanwhile, the US government issued warnings of widespread cyber threats against water systems, citing potential attacks by Iranian and Chinese hackers. These threats, if realized, could disrupt vital infrastructure and impose significant costs on affected communities, underscoring the importance of robust cybersecurity measures.
Adding to the concerns, a new variant of Russian wiper malware, named AcidPour, has surfaced, targeting communication networks in Ukraine. This malware, believed to be an updated version of AcidRain, poses an increased threat with expanded capabilities to disable various devices, including networking and IoT systems.
In parallel, Chinese hacker groups continue to pose a significant cybersecurity risk globally. Earth Krahang, in particular, has targeted numerous organizations across 48 countries, with a focus on government entities. Utilizing methods such as spear-phishing and exploiting vulnerable servers, these hackers engage in espionage and further attacks, highlighting the persistent and evolving nature of cyber threats.
On the privacy front, concerns are raised regarding the extent of data sharing by websites, with some sites found to share user data with over 1,500 third parties. Additionally, platforms like Glassdoor are shifting towards real-name usage, signaling a potential shift away from anonymous online interactions.
These developments serve as a stark reminder of the complex and ever-evolving landscape of cybersecurity threats, underscoring the need for vigilance and proactive measures to safeguard digital infrastructure and user privacy.










Discussion about this post